Create a human firewall
There is no technological solution that solves all security risks. Companies must ensure that they’re not just investing in technology, but are also creating a security-conscious workplace culture. The key to securing users is to empower them to realize that they’re an important part of the company’s cybersecurity plan and to show them what they can do to become an effective human firewall.
This human firewall has three main components: employee education, minimizing human error, and getting ahead of new threats. But the main objective of creating a human firewall is to raise the awareness of end users or employees to such an extent that they become a solid line of defense against attempts to compromize your systems or organization. Building a human firewall is more than just providing one-off security training, and it’s more than telling your users what’s bad. A human firewall seeks to stop humans from being the weak point in organizational security by upgrading users to think securely. That’s why we do our best to make the training fun and engaging.
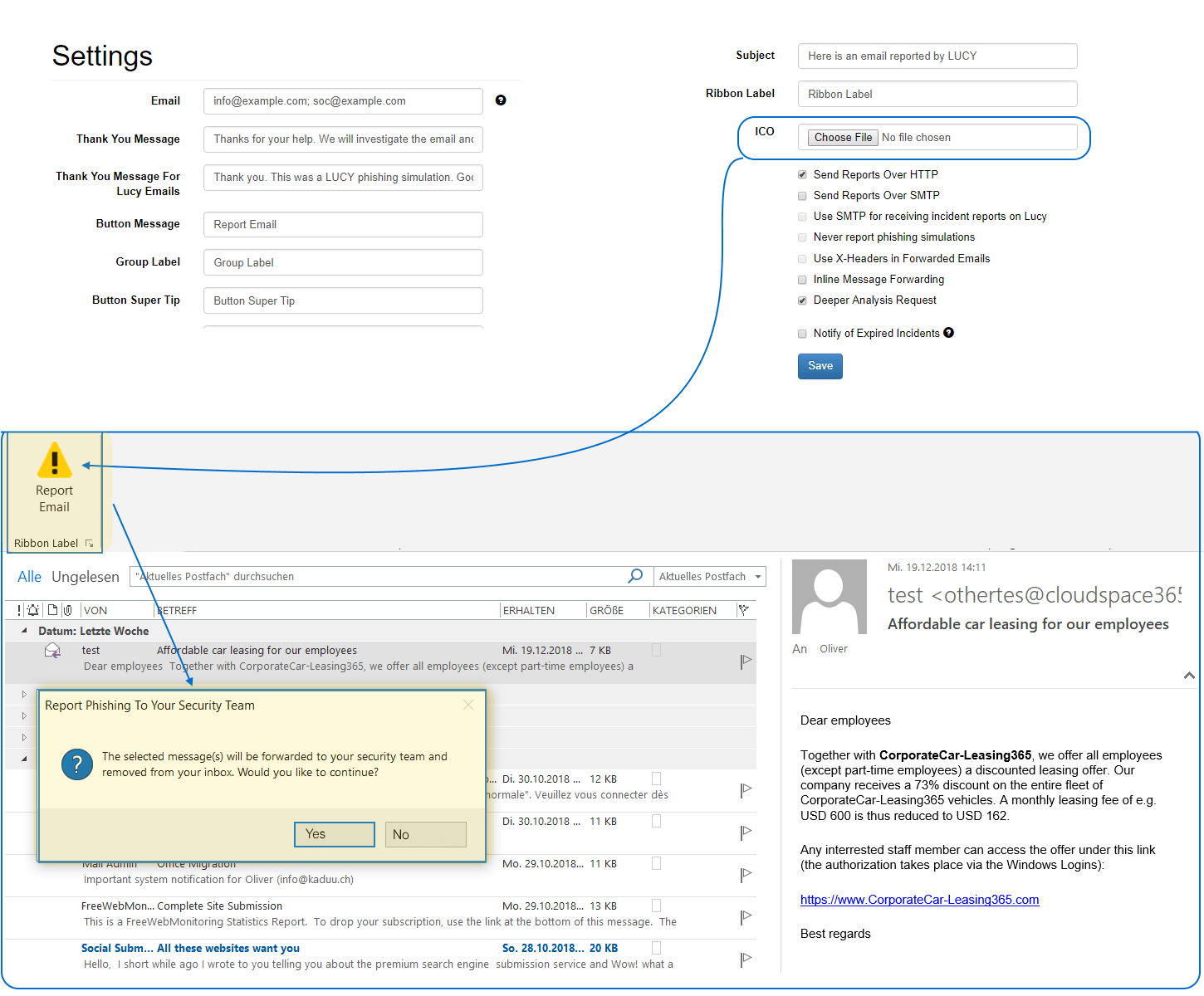
End users can report suspicious e-mails with a single click to one or multiple e-mail accounts and have them forwarded to your LUCY incident analysis console.
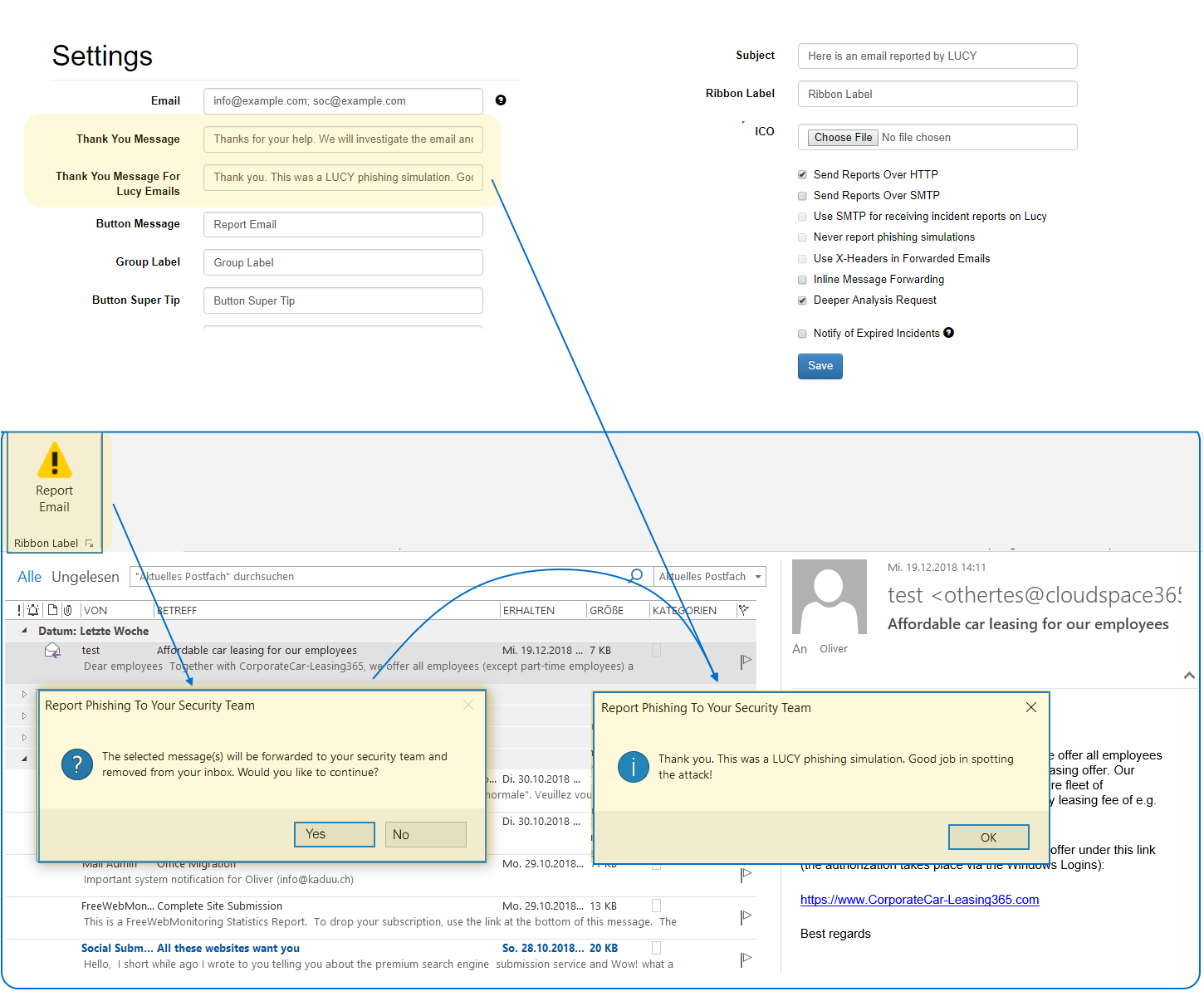
Our plugin automatically provides positive behaviour reinforcement by showing gratitude to end users via a custom message defined by your organization.
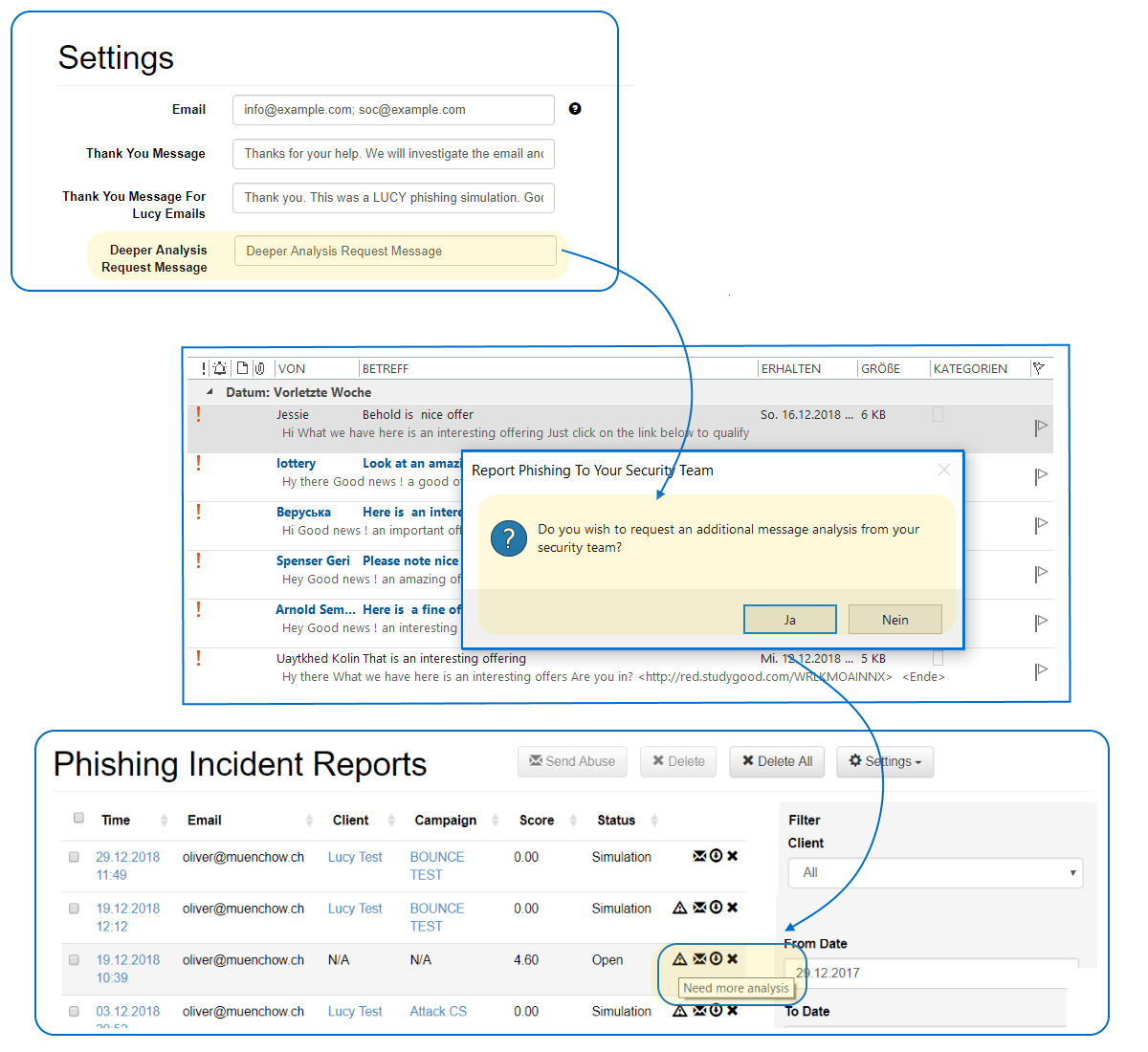
Sometimes users want to know if the received e-mail can be opened safely. The user can optionally use the “deep inspection request” within the local plugin to tell the security team that he wants feedback on the reported e-mail.
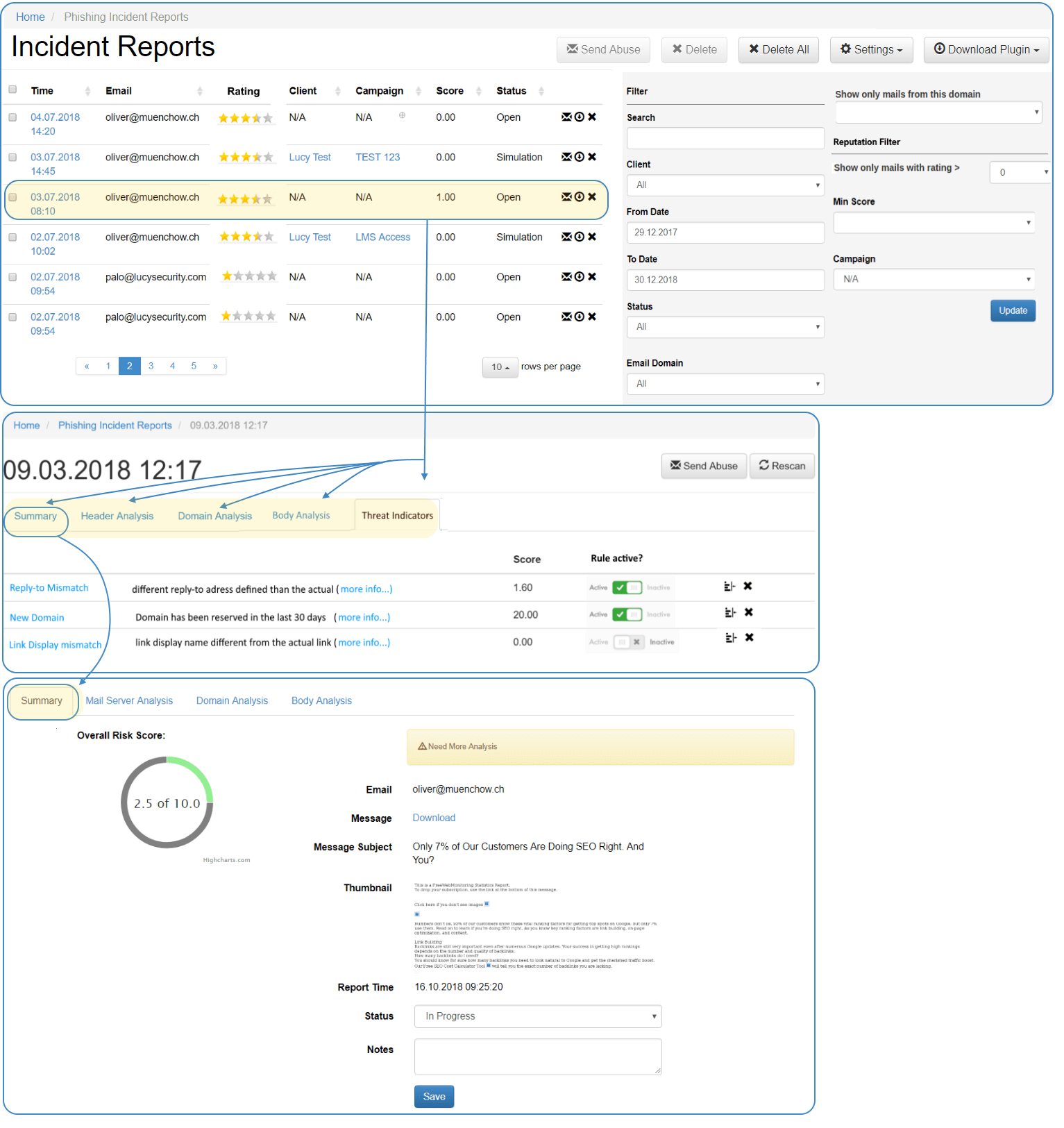
Manage and respond to reported suspicious e-mails using a centralized management console: Lucy analyzer allows an automated inspection of reported messages (header & body). The analyzer includes an individual risk score, providing a real-time ranking of reported e-mails. The Threat Analyzer brings a noticeable relief for the safety team’s work load.
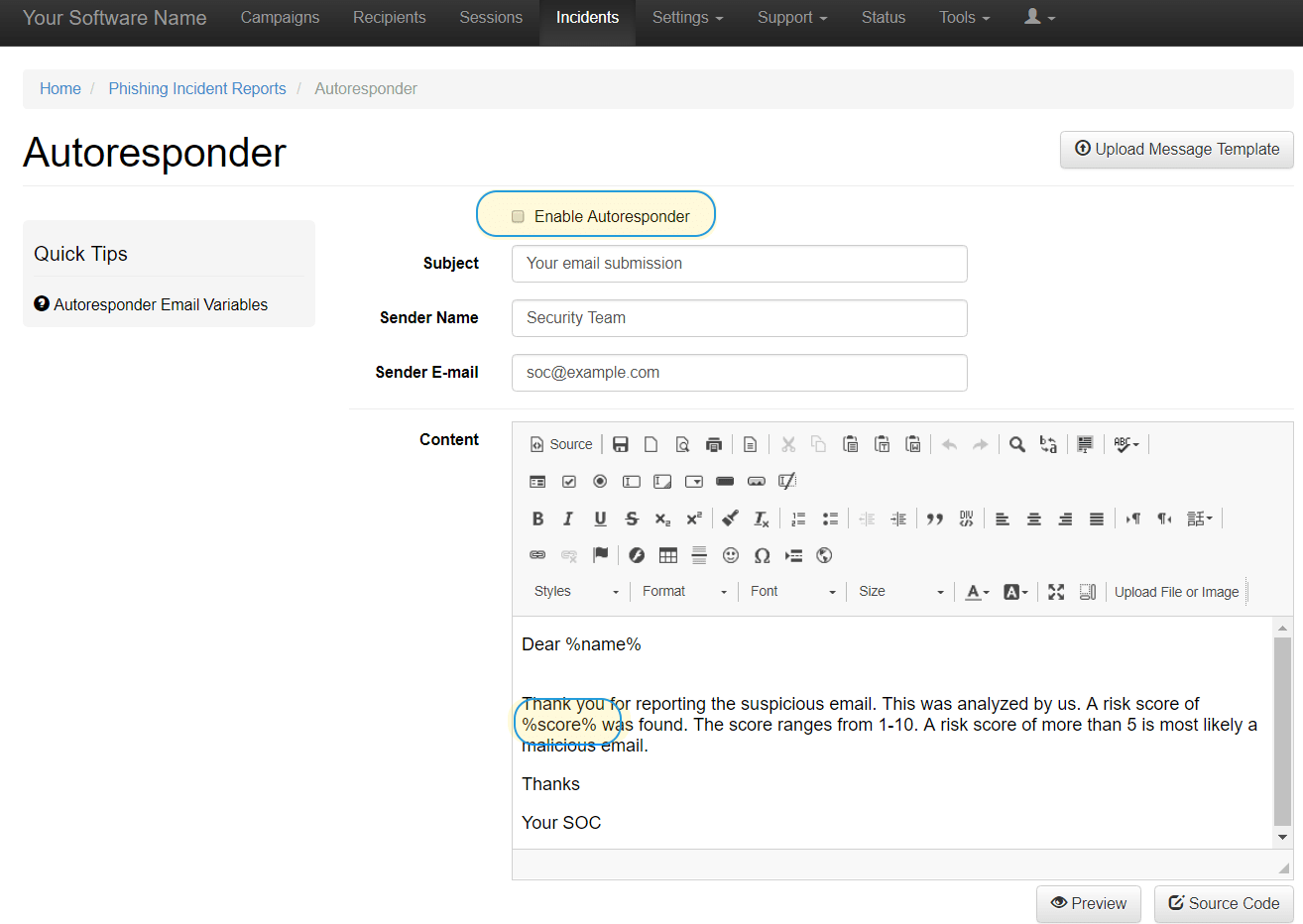
The Incident Autoresponder allows sending an automated notification to the end user providing the results of the e-mail threat analysis. The message text is freely configurable, and the LUCY E-mail Risk Score can also be included, if required.
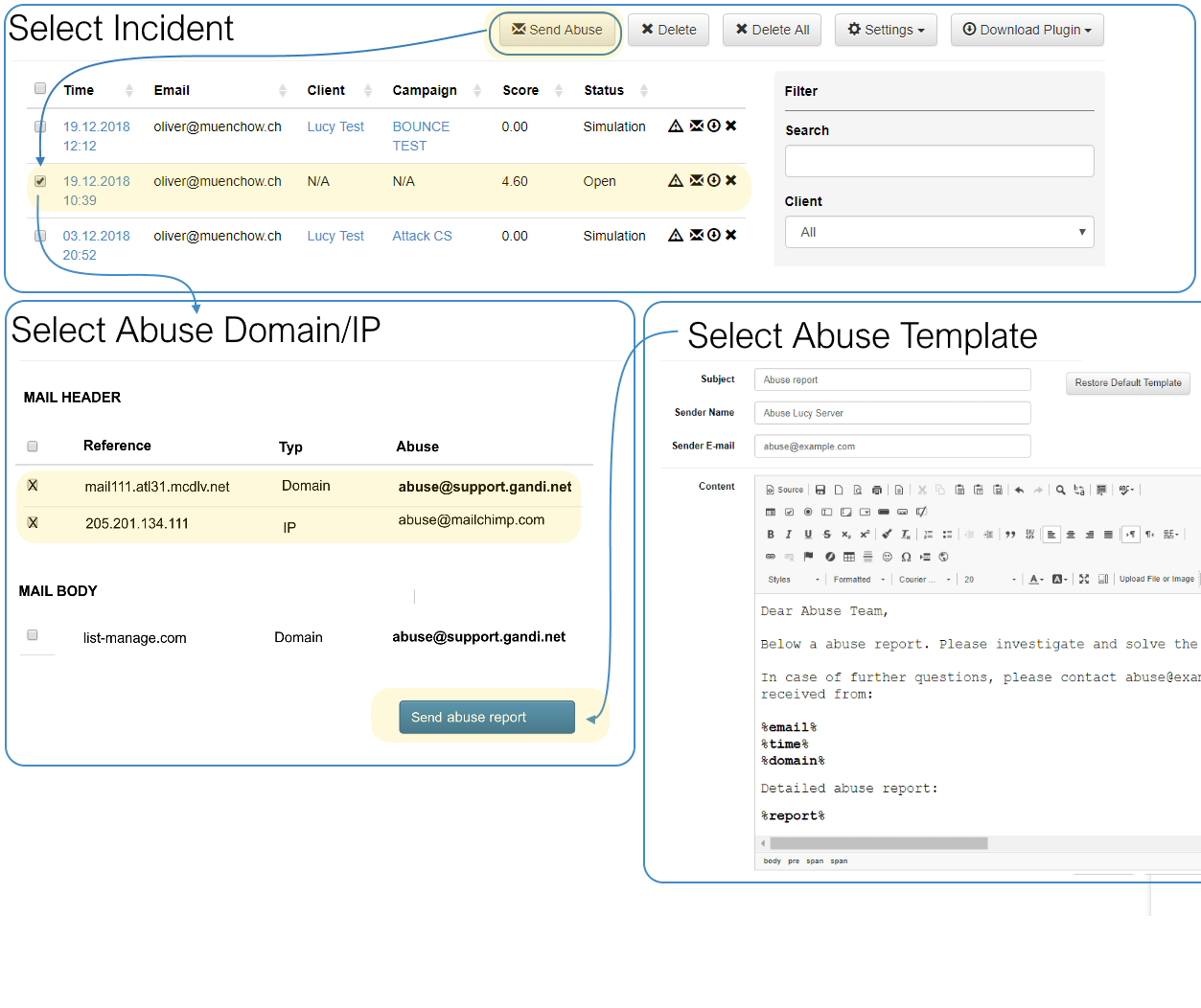
The behavioural threat mitigator is a revolutionary approach to eliminating e-mail risks. It will support the security admin in shutting down the attack (e.g., sending an automated report to specified abuse team of providers involved in the attack).
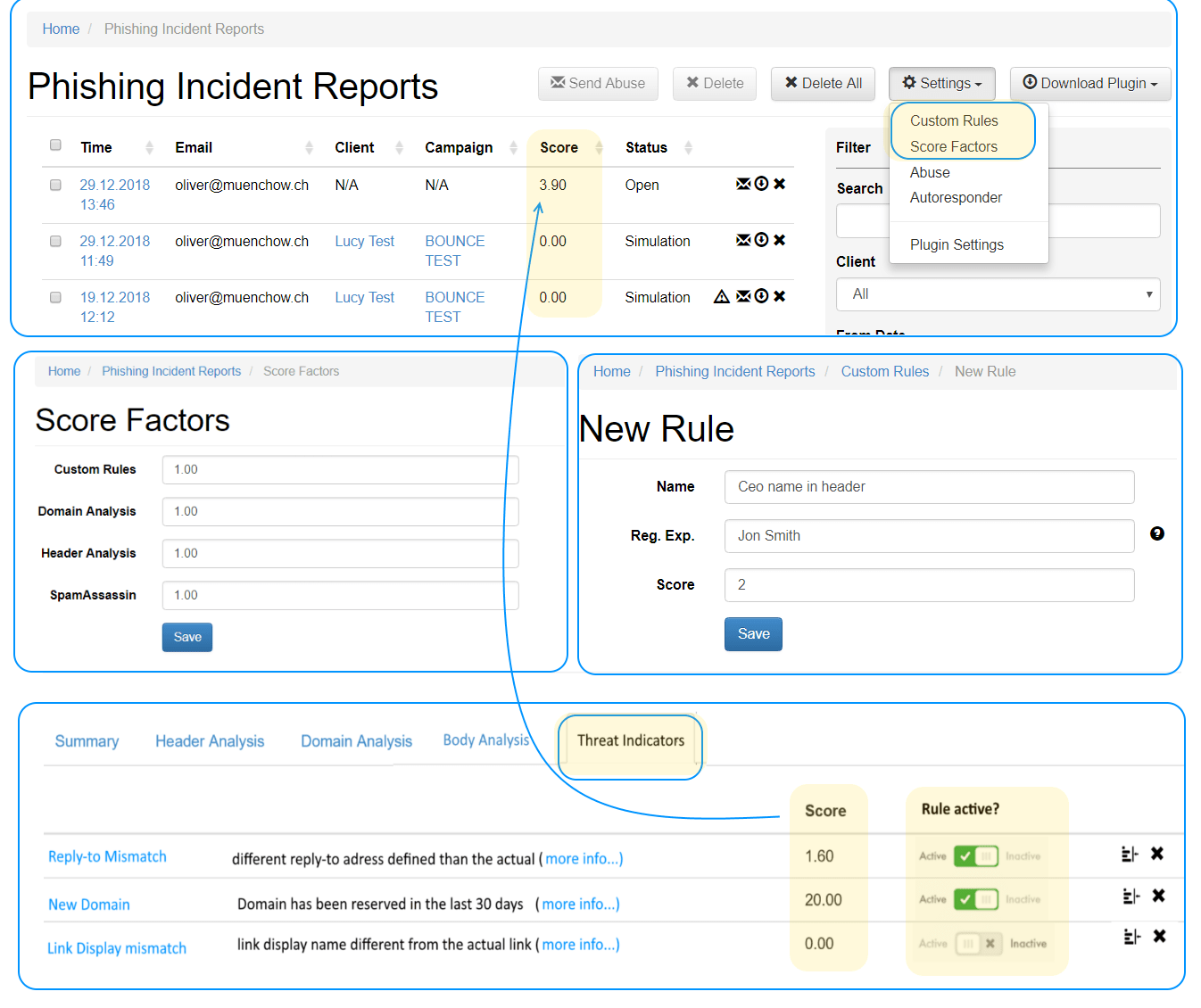
Define your own rules for e-mail analysis and risk calculations.
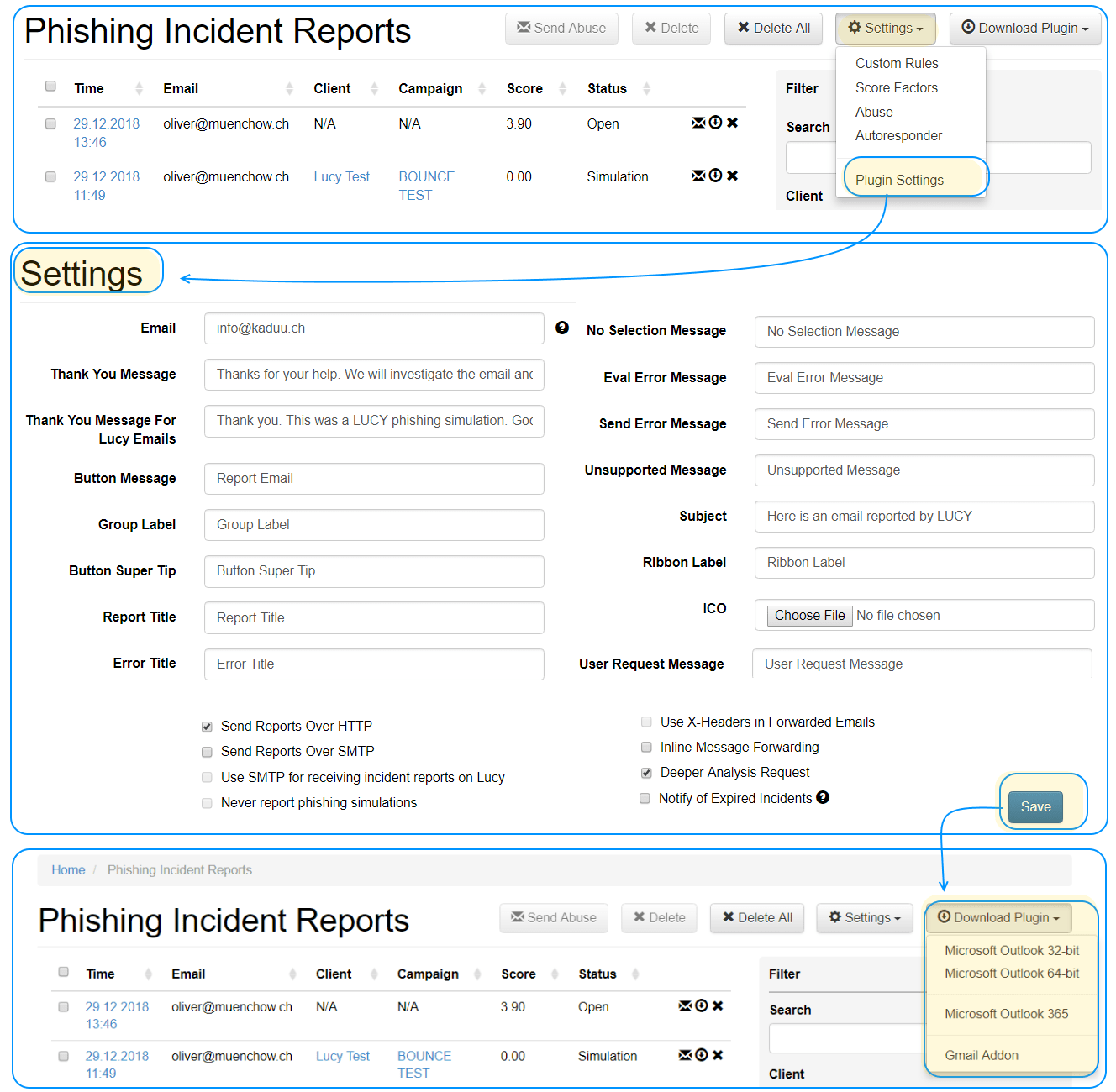
LUCY allows an easy customization and a complete white labelling of various plugin functions (displayed icon, feedback messages, ribbon label, transmission protocol, sent header, etc.).
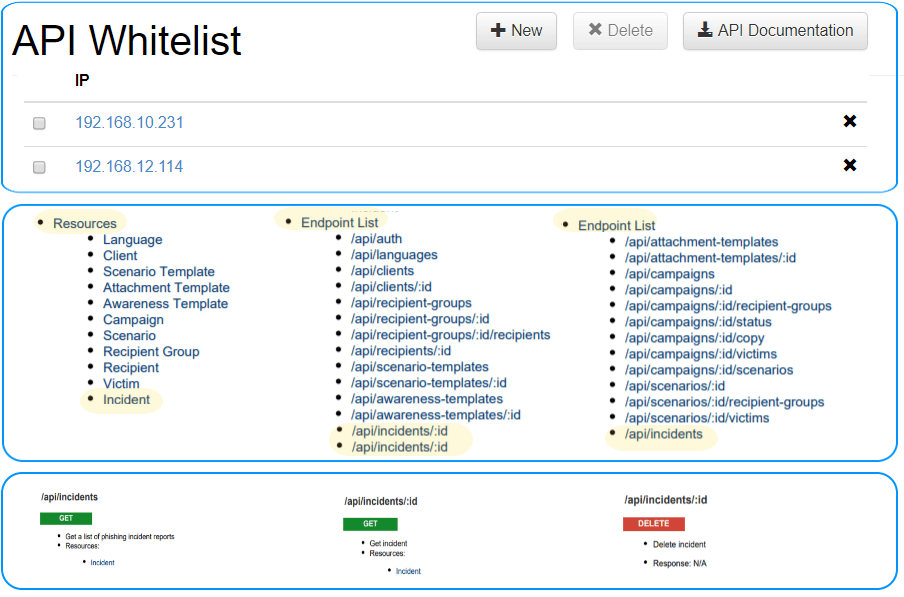
Using LUCY’s incident REST API automation, we can process reported e-mails and help your security team stop active phishing attacks while in progress.
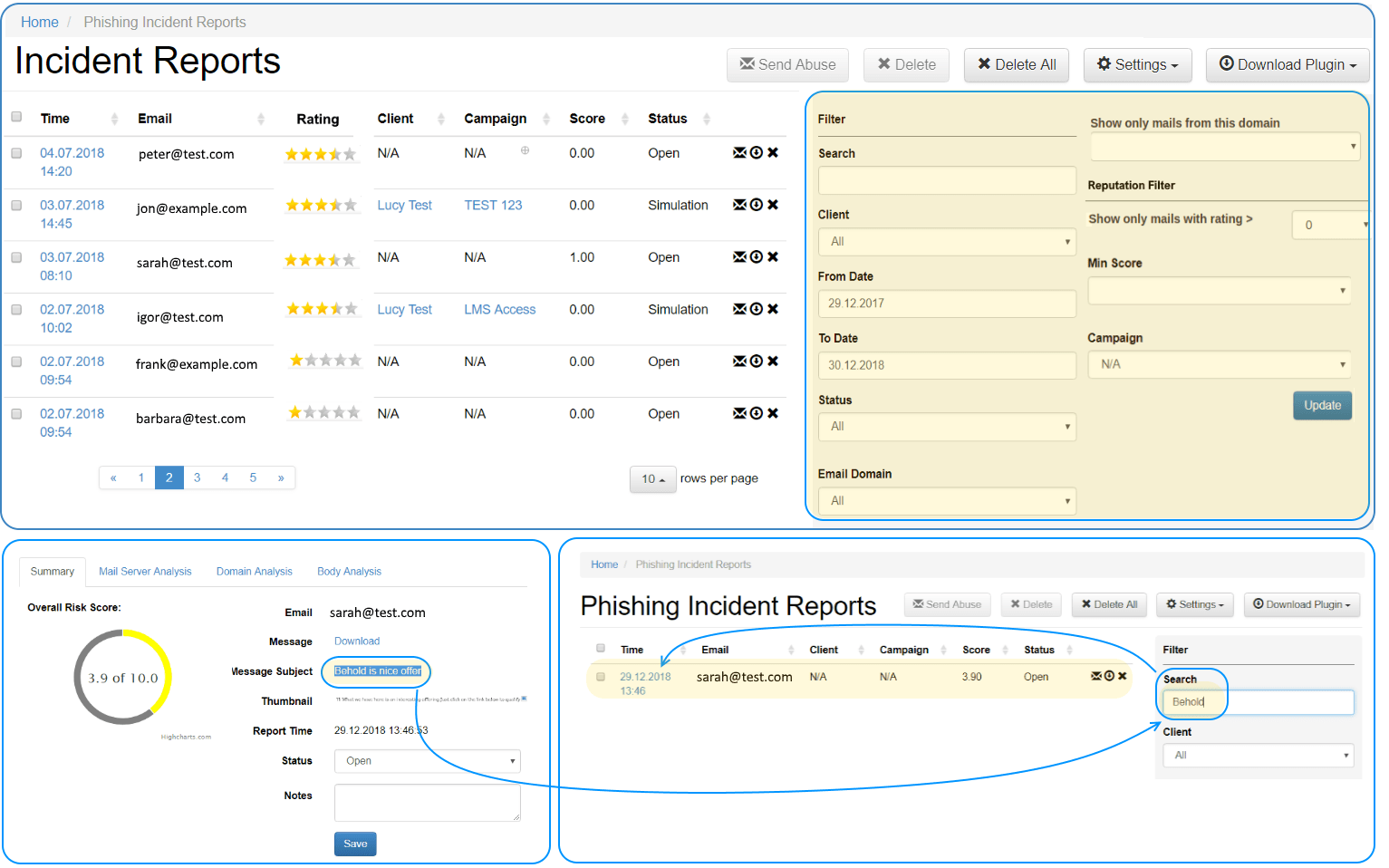
Apply LUCY’s dashboard filters to detect common attack vectors across your organization. Search within all reported e-mails for similar indicators of compromise.
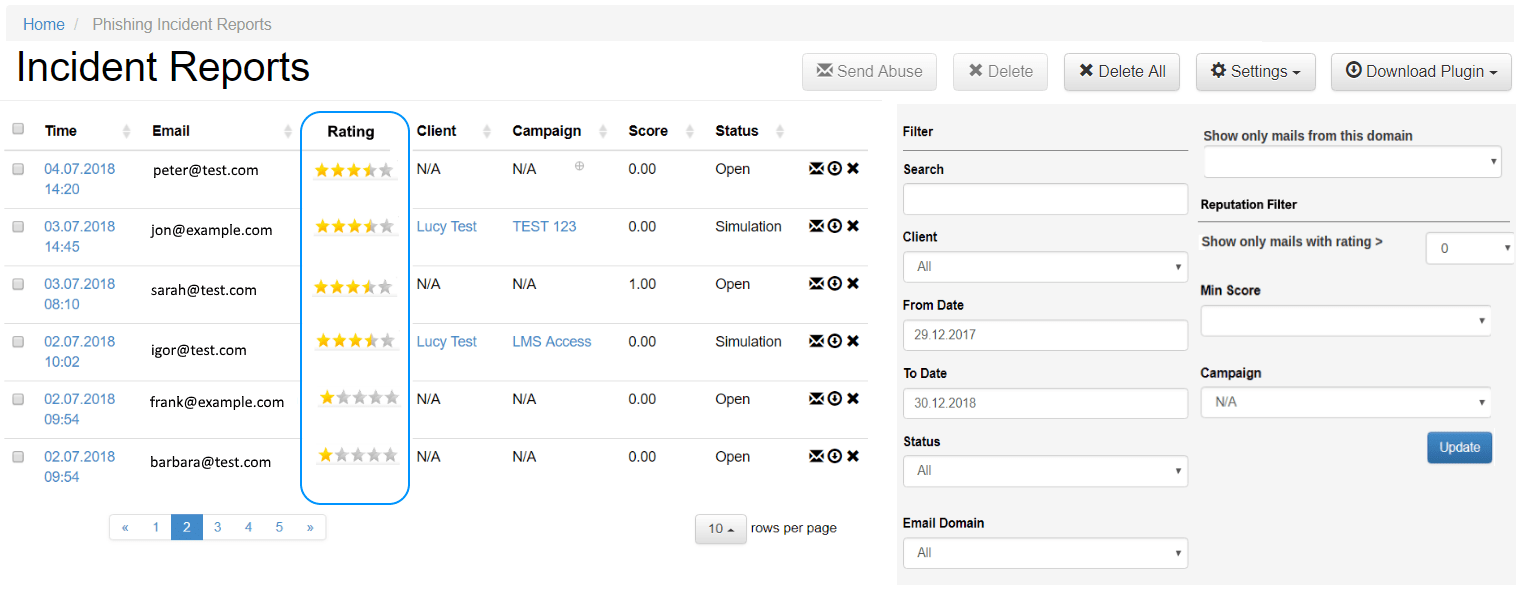
Classify users with an incident reputation score.
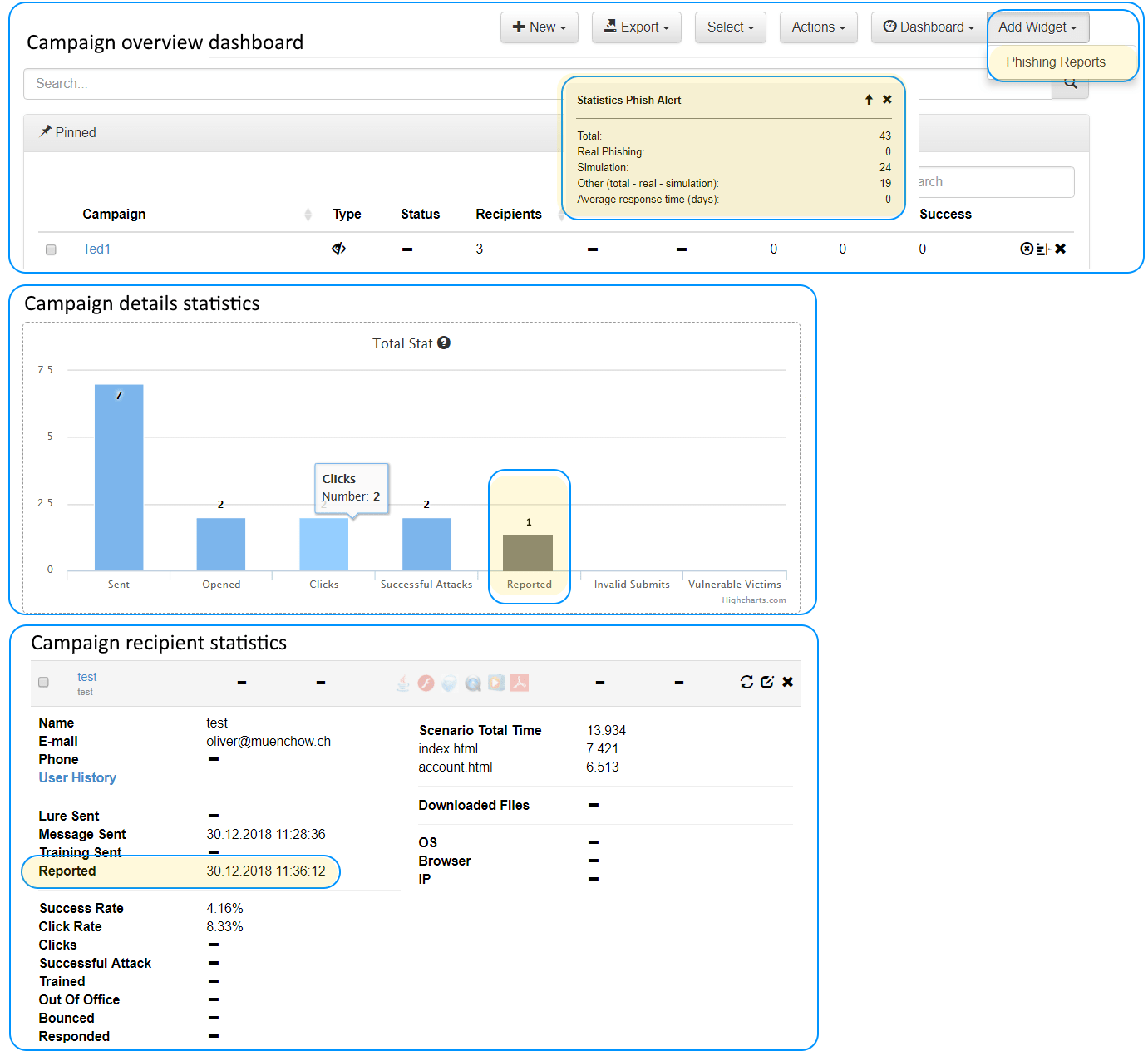
Seamless report and dashboard integration with phishing simulations: identify the users who have behaved exemplarily in a phishing simulation.
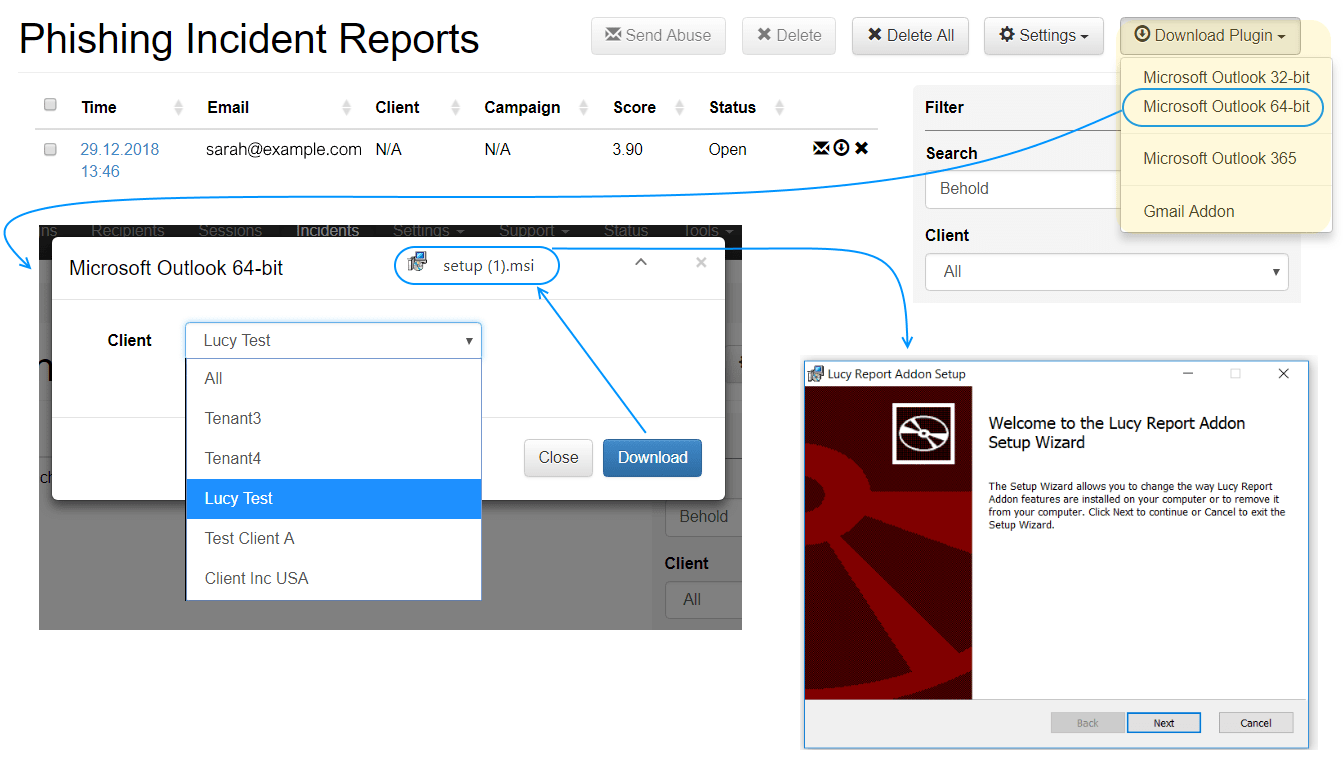
Install the Phishing Incident Plugin for Outlook, Gmail, Office365.
Address:
Lucy Security AG
Hammergut 6
6330 Cham
Switzerland